Fingerprint browsers are likely familiar to anyone doing cross-border business. They can simulate and manage multiple different browser environments to prevent websites or platforms from recognizing the same user. Many users wonder when using a fingerprint browser: is the generated fingerprint really authentic? How can it be verified?
Verifying the authenticity of a fingerprint is actually quite simple. You can use fingerprint testing sites to check whether the generated environment fingerprint matches the data of a real device.
This article will focus on how to use fingerprint detection tools to verify the authenticity of browser fingerprints, as well as common reasons for anomalies and solutions.
Why should you care about the authenticity of fingerprint browser environments?
The main purpose of a fingerprint browser is to simulate different device environments and provide independent usage scenarios for multiple accounts. For example, e-commerce or social media managers may need to manage multiple Instagram, Amazon, or Facebook accounts. If the fingerprint environment is "not authentic," the following risks may occur:
1. Account anomalies or bans
If a platform detects abnormal browser fingerprints, it may easily assume bulk operations, triggering platform risk controls and resulting in multiple accounts being linked or banned.
2. IP or device mismatch
Even if you use a proxy IP, if the browser fingerprint shows a timezone, language, or hardware info inconsistent with the proxy country, it may still be identified as the same user, leading to account suspension.
Therefore, verifying the authenticity of a fingerprint browser environment is essential for the safe operation and management of multiple accounts.
How to check if a fingerprint browser environment is authentic?
The most common method to determine if a fingerprint environment is real is using a browser fingerprint detection tool. These tools can collect and display various parameters of your current browser.
There are many fingerprint testing websites available. Here are two recommended options:
1. ToDetect
ToDetect is one of the most comprehensive browser fingerprint detection tools. It provides an advanced method to fully analyze browser fingerprint information, including browser version, screen resolution, fonts, language, plugins, IP address, and more than 50 other attributes. It can also detect if WebRTC leaks your real IP, helping users assess privacy risks.
Additionally, ToDetect offers the following practical features:
IP address lookup
Network speed test
DNS leak test
User-Agent analysis
Port scan
Bot detection
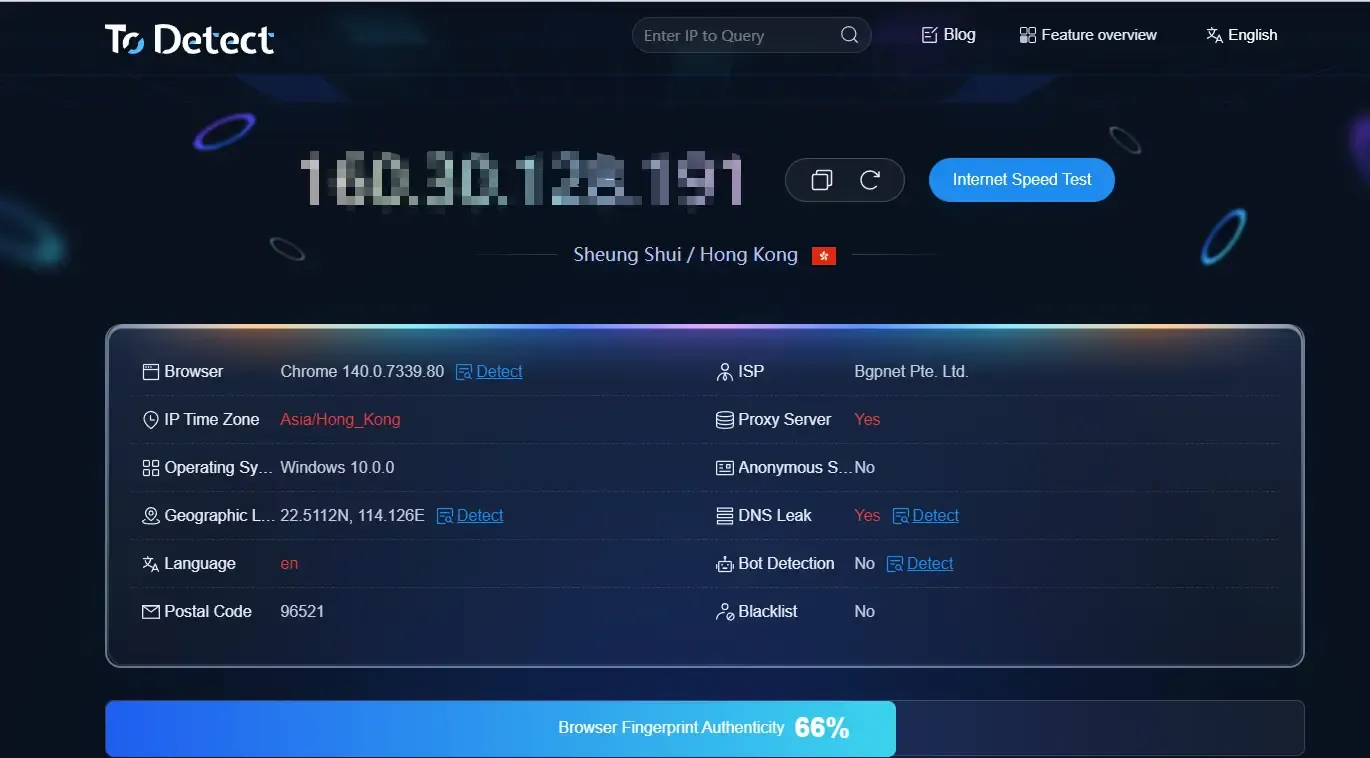
How to evaluate the fingerprints generated by a fingerprint browser?
You can use ToDetect to verify the fingerprints generated by MostLogin fingerprint browser. Simply create and open a browser environment in MostLogin, visit todetect.net, and you will see a complete fingerprint report.
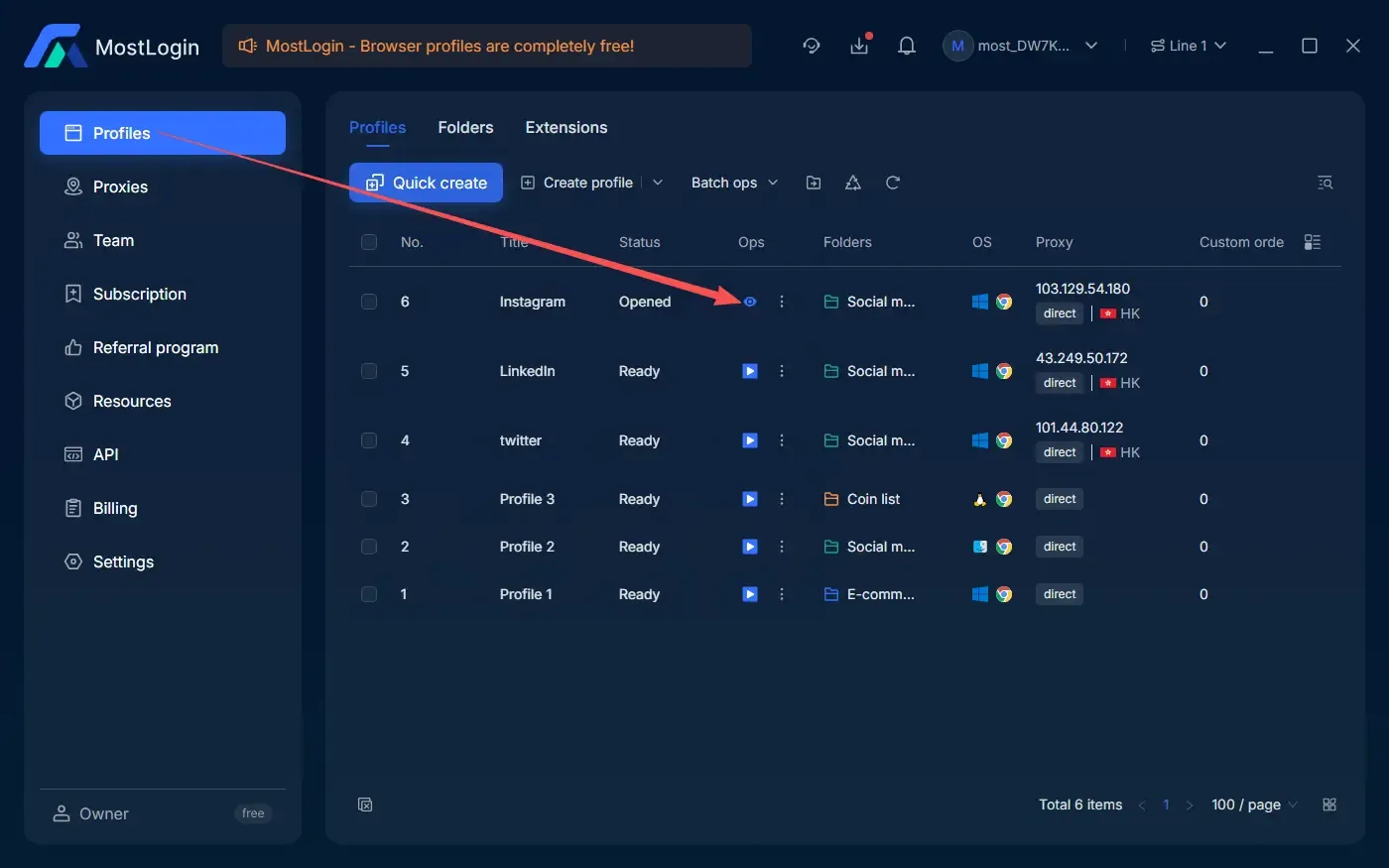
ToDetect provides a quick analysis, giving you detailed insight into the currently opened browser fingerprint. If any fingerprint parameters appear abnormal, they are usually highlighted in red.
Key detection information includes:
IP address
Browser version
IP timezone
Network provider
Operating system
Proxy server
Location (country, coordinates)
Bot detection
Postal code
Language
Additionally, ToDetect provides a real score for your browser fingerprint. If it is below 90, there may be anomalies or leakage risks, and it is recommended to check the detailed report further.
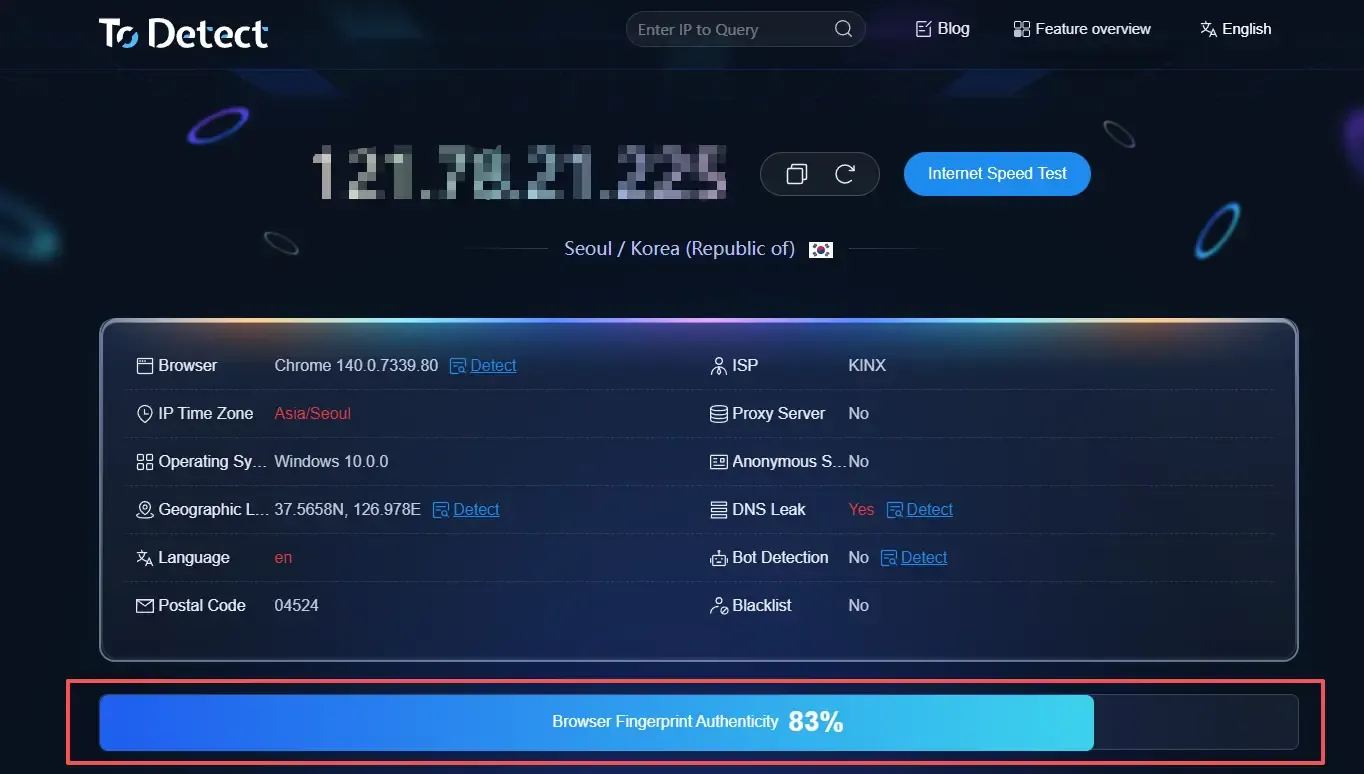
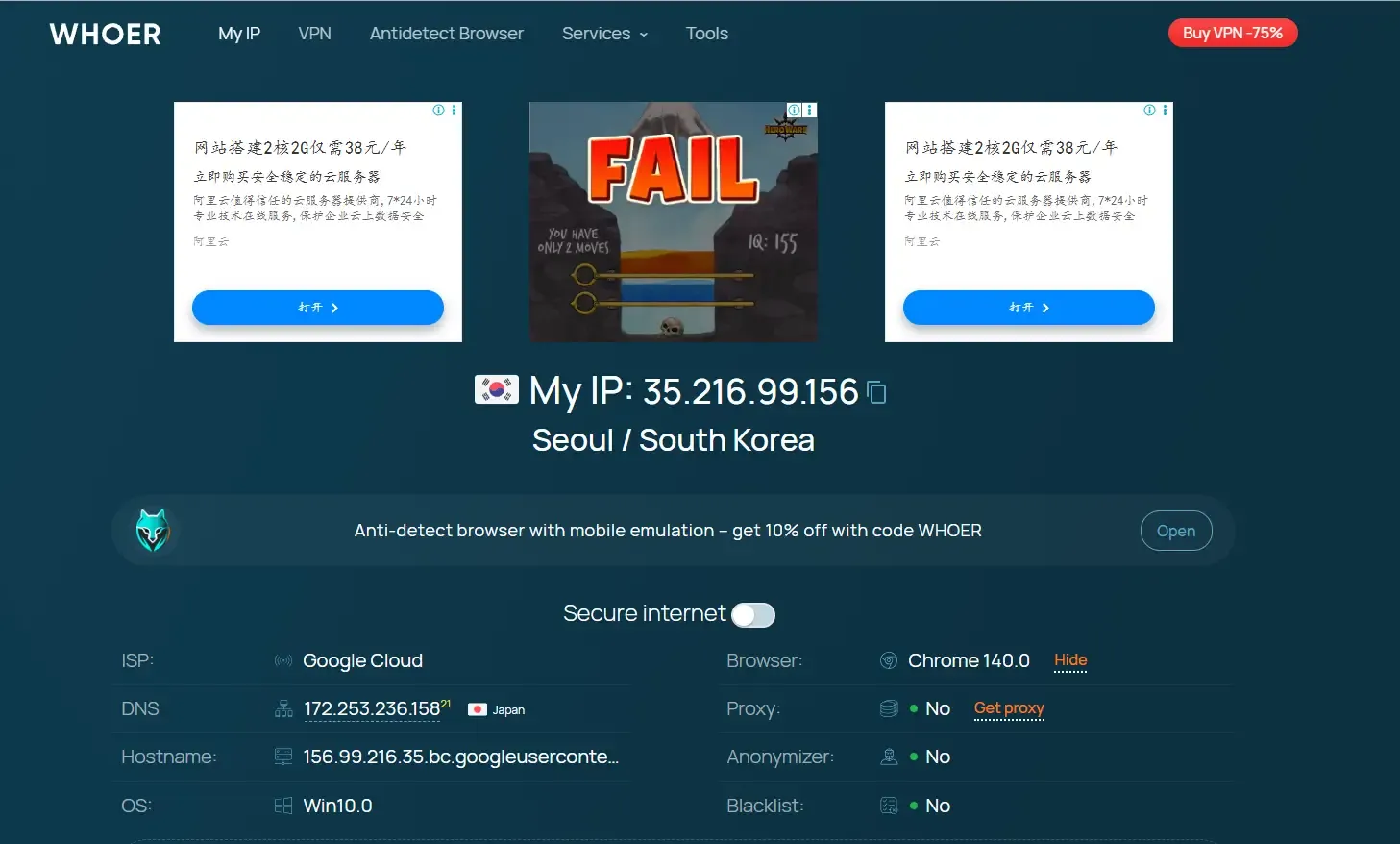
2. Whoer.net
Another fingerprint testing site is https://whoer.net/, an online tool for checking IP, proxy, and browser fingerprint anonymity.
Common fingerprint detection anomalies and solutions
When detecting fingerprint browsers, many users notice anomalies in the reports. These often indicate that the fingerprint is not sufficiently "real."
Verification using ToDetect:
MostLogin generates a unique browser fingerprint for each account. Cookies, cache data, browser plugins, and other browser environment files are isolated in separate folders. Even with hundreds of accounts, you can log in on the same device without interference, fully independently.
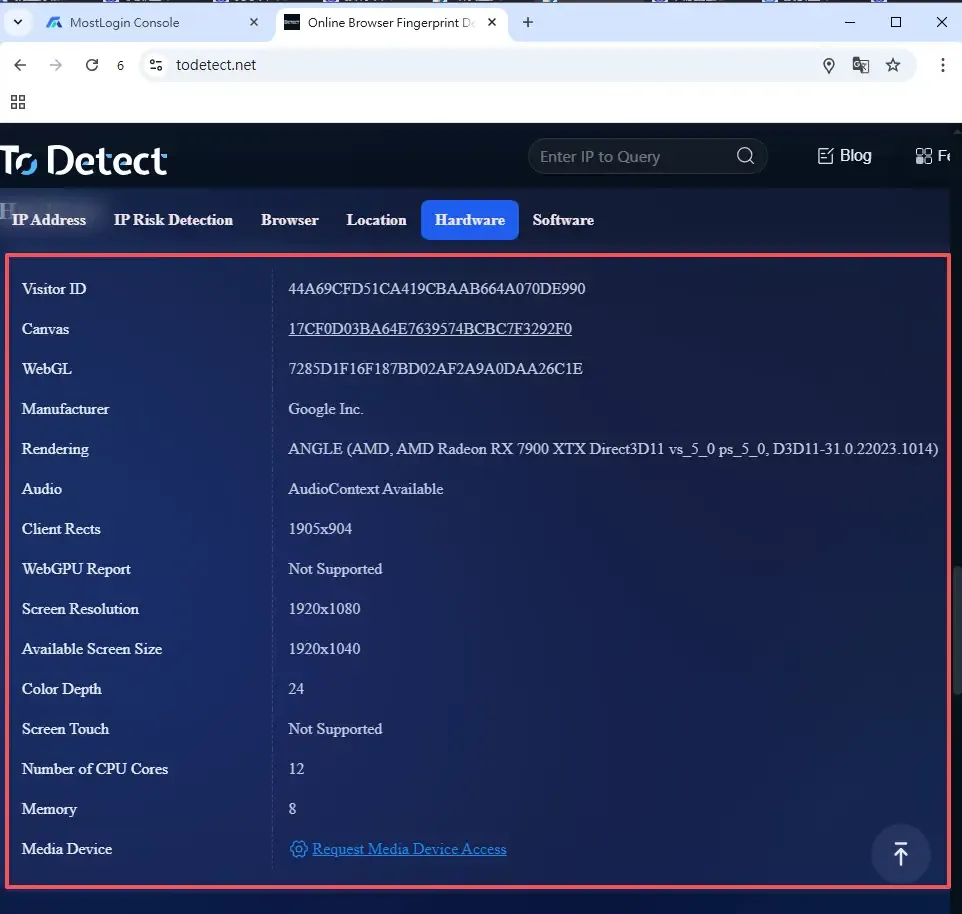
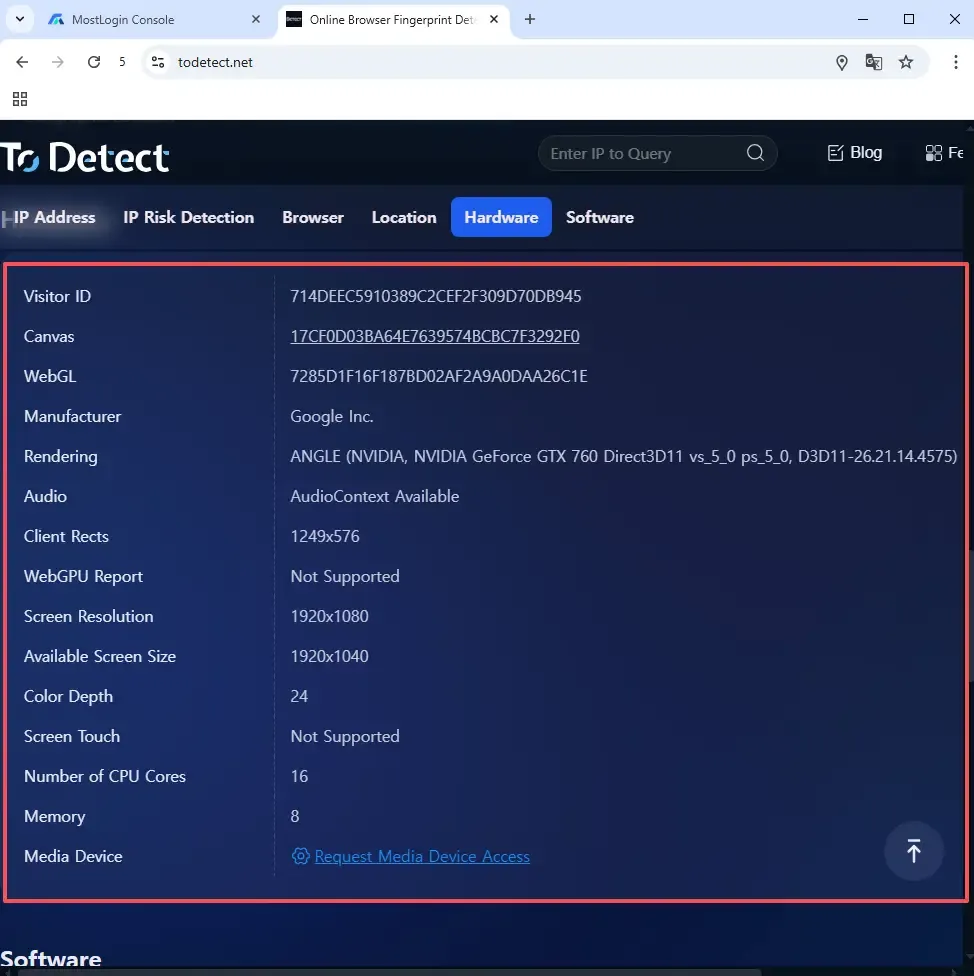
Occasionally, even when using MostLogin, third-party detection sites may still report fingerprint anomalies. This can be caused by multiple reasons. Here are some common causes and solutions:
Fingerprint parameter mismatch
Detection may fail if the generated environment differs from reality, causing inconsistencies in detection tools. For example, a User-Agent string and kernel version mismatch may cause detection failure.
Solution: Check fingerprint browser settings to ensure the UA string matches the kernel version. In MostLogin, update the kernel version or adjust the UA settings for consistency.
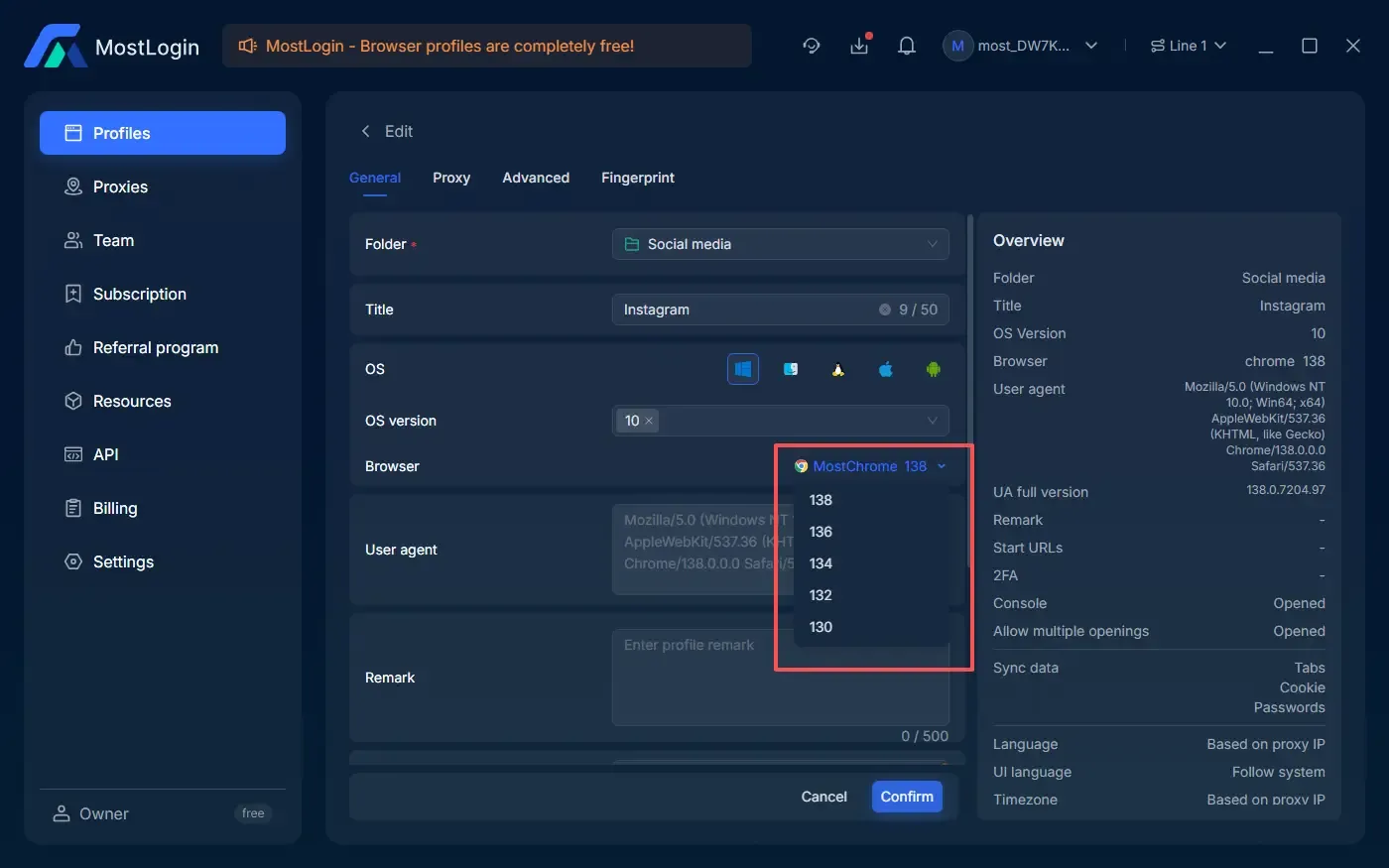
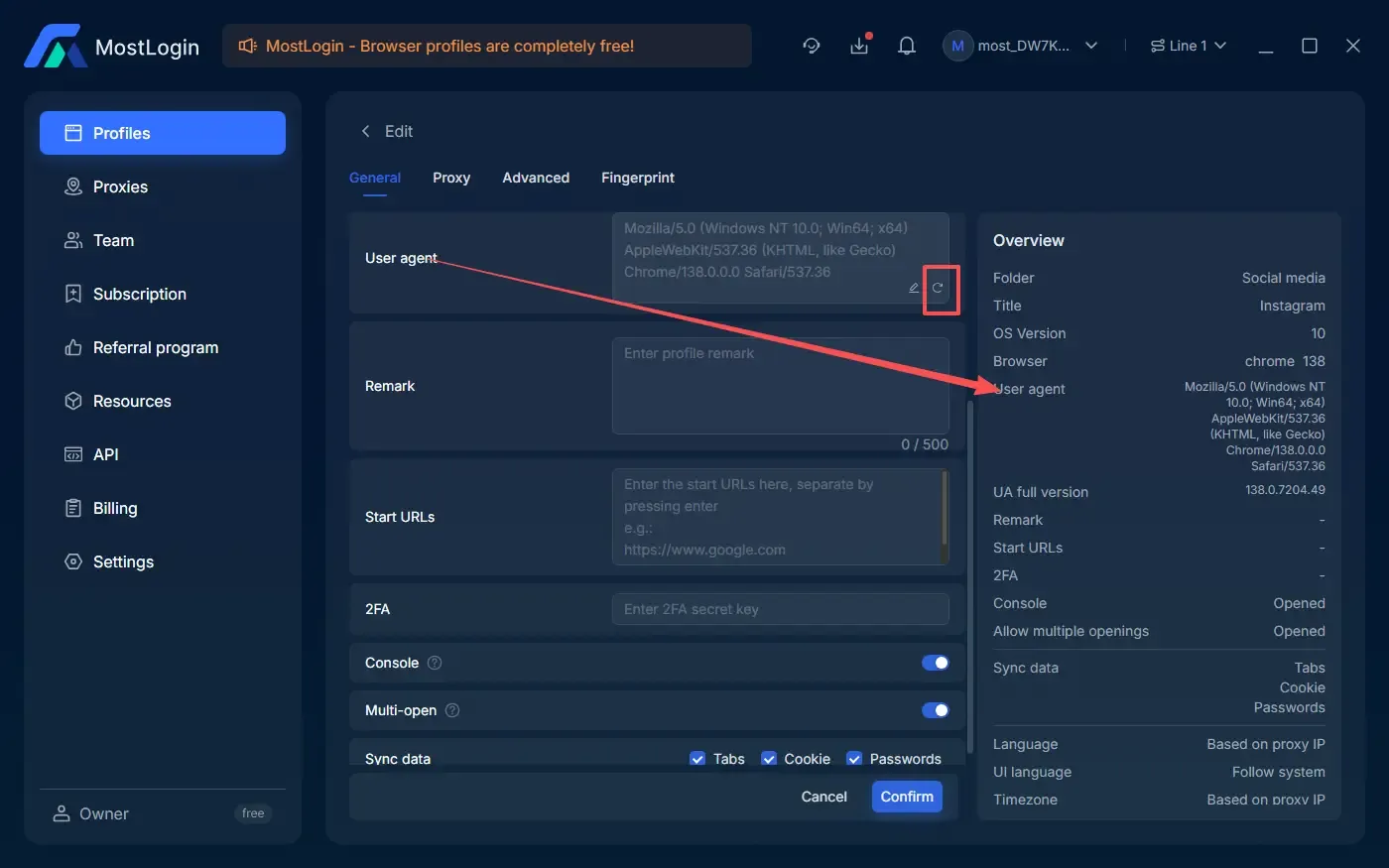
IP data mismatch
If IP detection fails, it is usually because different detection sites use different IP lookup methods, causing inconsistent results.
Solution: Choose a proxy service provider with frequent updates and high accuracy to reduce false detections.
Improper fingerprint browser settings
Settings that are unnatural or inappropriate may lead to abnormal feature combinations, triggering detection tools. For example, ToDetect checks whether WebRTC exposes the real IP, which can leak your IP address.
Solution: Verify that the IP matches the proxy and ensure WebRTC does not leak your real IP.
Plugin interference
Some third-party plugins can modify browser parameters, potentially overriding fingerprint browser settings and causing conflicts.
Solution: Avoid using plugins that change browser behavior or add custom request headers to ensure they don’t interfere with fingerprint consistency.
GPU information mismatch
Sometimes hardware test anomalies occur, such as displaying a Mac GPU in a Windows environment.
Solution: Ensure hardware parameters in the fingerprint browser match the target device. In MostLogin, GPU info can be manually adjusted to simulate real GPU data.
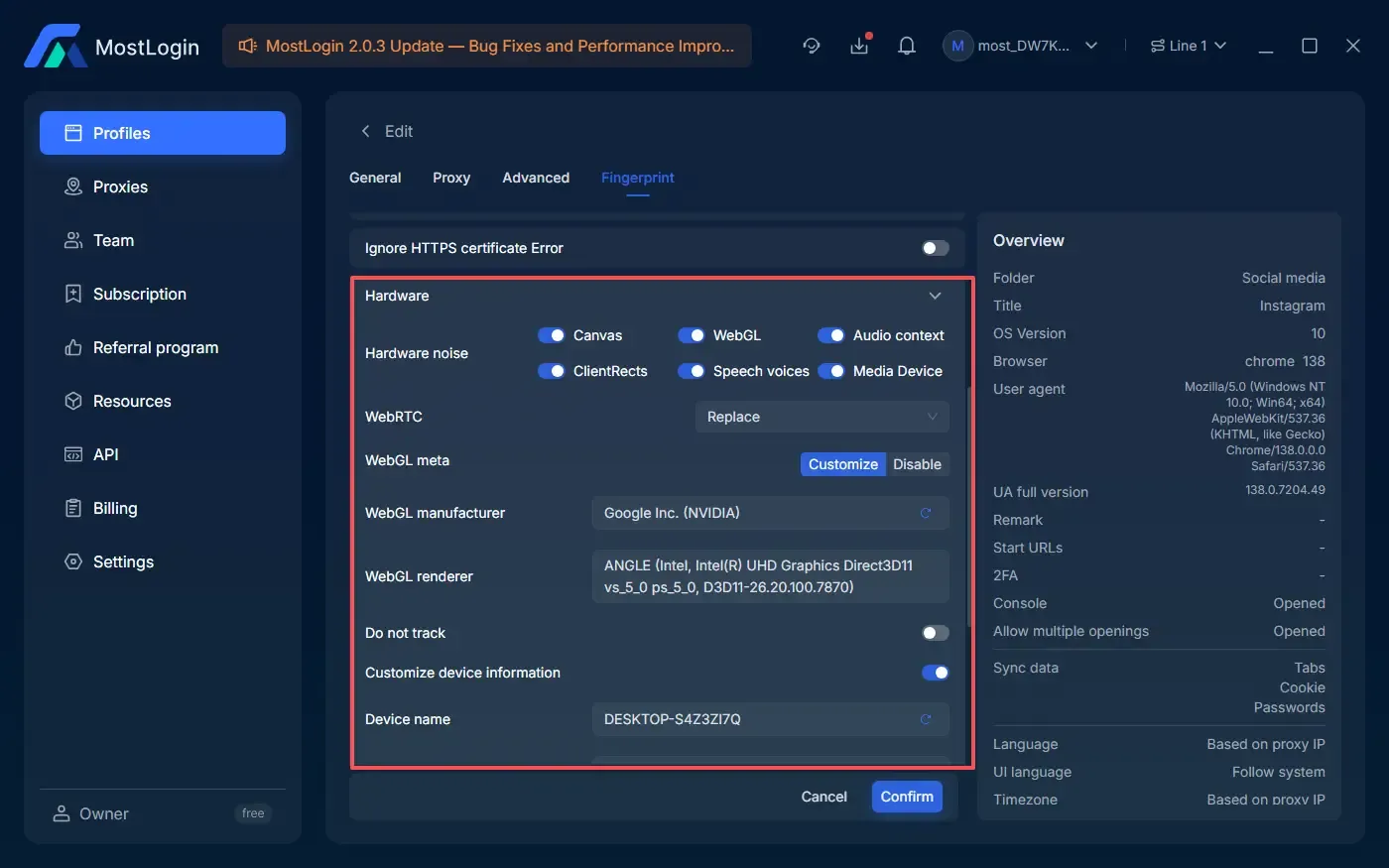
How to optimize the authenticity of fingerprint browsers?
Users can optimize the fingerprint browser environment in the following ways:
1. Configure timezone and language appropriately
The timezone, system language, and browser language should match the proxy country. For example, if you choose a US proxy, set the language to English (en-US) and timezone to UTC -5 or UTC -8.
2. Choose high-quality proxy IPs
Ensure the proxy IP matches the target market and use residential IPs for a more realistic user environment.
3. Simulate common device fonts and plugins
Add common fonts and extensions to the browser environment to make it resemble a typical user.
Conclusion
Verifying the authenticity of a fingerprint browser environment is not complicated. Simply use fingerprint detection tools to check if IP, timezone, language, Canvas, WebGL, and other parameters are reasonable and consistent, and you can quickly determine authenticity.
If anomalies are found, optimize proxy IP, system configuration, language, timezone, fonts, and plugins. Ensuring the environment closely resembles real users helps minimize risks in multi-account management.
Additionally, to maintain clean fingerprints, choosing a reliable fingerprint browser is crucial. We recommend using MostLogin (free browser environment usage) to generate unique browser fingerprints for each environment, reducing fingerprint anomalies and ensuring environments are both authentic and detection-resistant.
🚀 Best Fingerprint Browser - MostLogin
MostLogin fingerprint browser helps users solve high-frequency issues such as multi-account management, environment isolation, and account risk control.
For operational guidance, please refer to the official help documentation