In today's Internet environment, users are increasingly concerned about personal privacy and data security. Especially in cross-border e-commerce, social media operations, and cybersecurity, "whether IP addresses are exposed" is a top concern.
Many users find that even when using proxy IPs, VPNs, or fingerprint browsers, their real IP addresses can still be exposed in certain detection tools, leading to large-scale account anomalies or even bans. This often relates to WebRTC.
So, what is WebRTC? Why does it cause real IP leaks? And how can it be prevented? This article will explain these aspects in detail.
What is WebRTC?
WebRTC, short for "Web Real-Time Communication," is an open-source project launched by Google. Its goal is to enable browsers to directly handle audio and video calls, data transmission, and other real-time communications without relying on intermediate servers.
Its advantages include:
Supports real-time transmission of audio, video, and data
Enables direct browser-to-browser communication without third-party plugins or software
Provides high security, including end-to-end encryption
Seamlessly integrates with existing communication protocols and APIs
Why does WebRTC cause real IP leaks?
Many users may be puzzled: Even though I'm using a proxy IP or VPN, why can detection tools still show my real IP address? This is actually a WebRTC leak issue.
WebRTC Connection Principle
In peer-to-peer communication, WebRTC needs to know the actual network addresses of both parties. To achieve this, it:
Uses STUN/TURN servers to obtain the device's public and local IP addresses;
Exposes these addresses to browser JavaScript scripts for quick connection establishment.
Leak Manifestation
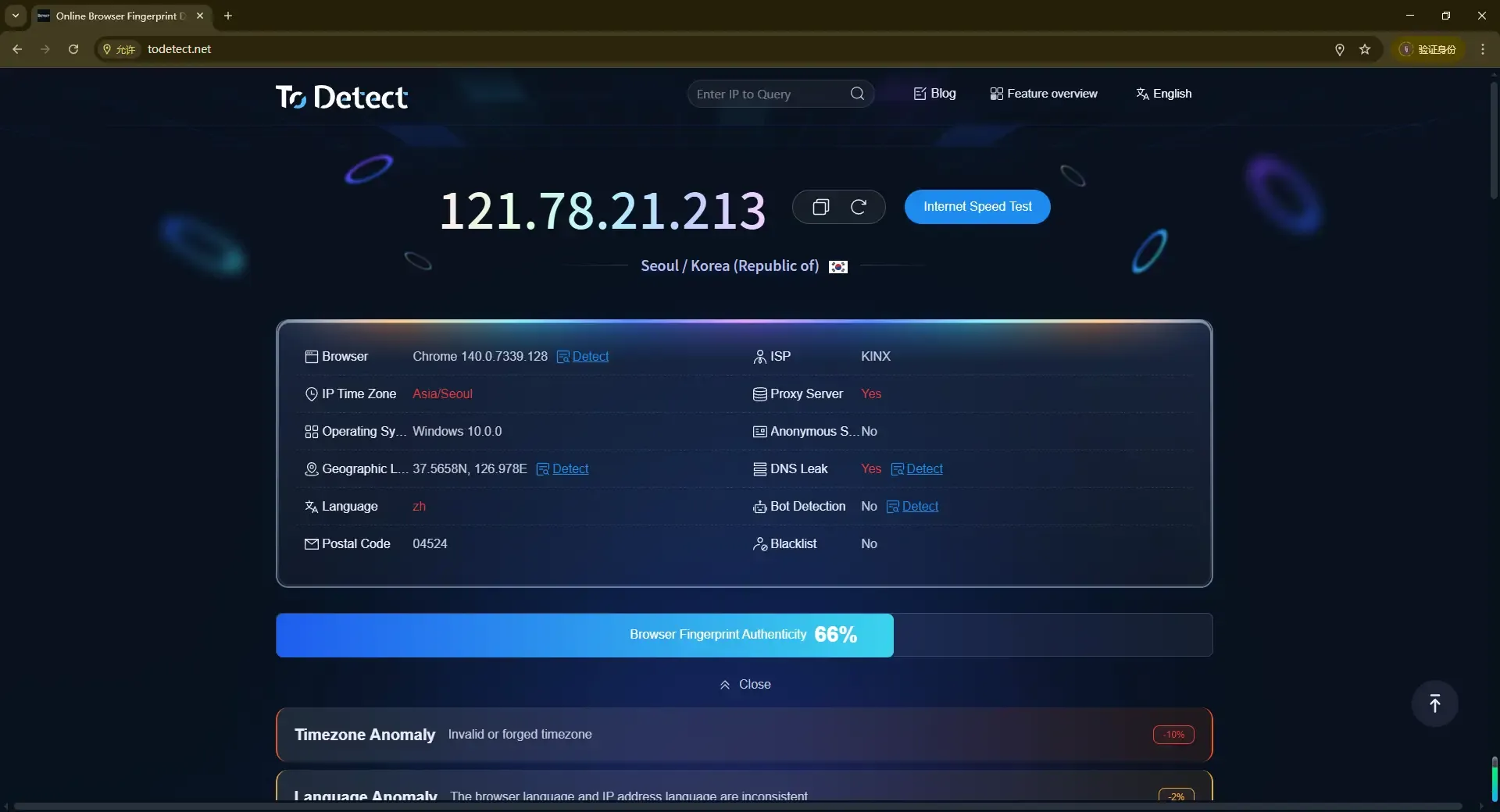
When you visit certain fingerprint detection websites (like ToDetect, Whoer, ipleak.net), they call the WebRTC API to obtain your real IP address, which often bypasses proxies or VPNs.
Risks
Account linking: E-commerce and social media platforms use IP addresses to determine whether multiple accounts belong to the same user;
VPN/Proxy failure: Even if using a proxy, platforms may still capture your real IP;
Privacy leaks: Attackers may use your real IP to track or attack you.
Therefore, when detection tools show "WebRTC leak," it indicates that the browser is exposing local network information even in a proxy environment.
How to detect if WebRTC is leaking?
1. Manually check browser WebRTC status
Chrome
Enter chrome://flags/#disable-webrtc in the address bar and check the settings to see if WebRTC is enabled.Firefox
Enter about:config in the address bar, search for media.peerconnection.enabled, and ensure the value is false, meaning WebRTC is disabled.
2. Use online detection tools
The easiest way is to use online detection tools, such as ToDetect. These tools are designed to detect whether your browser has WebRTC leak issues. Simply visit the site and start the detection process, usually with one click.
How to prevent real IP leaks via WebRTC?
Since the issue is WebRTC, the solution naturally is to disable or limit WebRTC.
1. Disable via browser settings
The disabling methods differ slightly among browsers
Chrome / Edge (Chromium-based)
Install extensions: such as WebRTC Control, uBlock Origin;
Or disable via startup parameter:
--disable-webrtc.
Firefox
Enter
about:configin the address bar;Search for
media.peerconnection.enabled;Set it to
false.
Safari
In "Preferences - Advanced - Develop," find "Disable WebRTC."
2. Use secure fingerprint browsers
For users who need bulk account management (cross-border e-commerce, social media operations), you can directly use fingerprint browsers with WebRTC protection features, such as MostLogin Fingerprint Browser. These browsers automatically block or spoof WebRTC information when creating environments, preventing detection of your real IP address.
3. Use high-quality proxies
Even if WebRTC is disabled, low-quality or frequently disconnected proxies can still cause platform detection anomalies. It is recommended to use residential IPs or highly stable proxy services to effectively work with WebRTC and prevent leaks.
Summary
WebRTC is essentially an advanced real-time communication technology that allows browsers to conduct audio, video, and data transmission without plugins. However, because it directly accesses local network interfaces, it can sometimes lead to real IP leaks, creating privacy risks.
By implementing the strategies above, we can leverage MostLogin's powerful features to maintain identity isolation across different online activities while enjoying the convenience WebRTC offers!
Frequently Asked Questions about WebRTC
Will disabling WebRTC affect browser usage?
In most cases, it will not affect normal browsing. However, if you need video conferencing, voice chat, or similar features, connections may not be established.
Why do multi-account operators need to pay attention to WebRTC?
Multi-account operators usually need to hide their activities and identities. WebRTC leaks may expose IP addresses, revealing account correlations.
Do I still need to disable WebRTC if using a VPN?
Yes. VPNs do not automatically prevent WebRTC leaks; many users are detected even when using a VPN.
Is WebRTC communication encrypted?
Yes, WebRTC uses end-to-end encryption to protect communication content, ensuring security during transmission.
References
Fingerprint Browser Rankings
What is Browser Fingerprinting? How to Clear It?
How to Determine if a Fingerprint Browser Environment is Real?
🚀 Best Fingerprint Browser - MostLogin
MostLogin fingerprint browser tools are dedicated to helping users solve frequent issues such as multi-account management, environment isolation, and account risk control.
For operational questions, please refer to the