Many people who manage multiple accounts may already use anti-association browsers, independent IPs, and virtual environments to avoid being identified by platforms, yet their accounts still end up being flagged for association by multiple platform systems.
You clearly followed all the precautions found online and thought everything was foolproof, so why still get detected? Actually, this is related to many factors. Today, from the perspectives of technology and platform risk control, we will explain how platforms identify account association.

I. What Information Do Platforms Identify?
Many users understand anti-association as simply having different browser fingerprints to prevent account linking. While browser fingerprints are indeed a core part of many platforms' association mechanisms, they are usually supplemented by other identification methods.
These include device environment, network characteristics, behavioral patterns, time regularity, and more comprehensive models. Browser fingerprints, though central, are only one component of the whole system.
II. Why Do Common Anti-Association Configurations Still Leak Information?
As mentioned earlier, accounts are still detected even after using anti-association browsers, independent IPs, and virtual environments, which may be due to incomplete settings in one of these aspects. For example:
1. Imperfect Fingerprint Spoofing Function of Anti-Association Browsers
Many anti-association browsers modify information such as User-Agent, Canvas Fingerprint, WebGL parameters, time zones, and languages. However, platforms with increasingly sophisticated mechanisms now identify much more information than that.
Current identification mechanisms also cover GPU driver layer features, system font rendering details, audio fingerprint differences, browser graphics stack calling modes, etc. Some anti-association browsers fail to achieve complete spoofing, leading to detection.
2. Poor IP Quality
Many people think changing proxy IPs guarantees security, but most platforms also analyze information such as the ASN (operator network) the IP belongs to, network latency characteristics, TCP/IP fingerprints, and DNS request paths.
If multiple accounts consistently use IPs from the same type, region, or with identical network characteristics, they may still be judged as controlled by the same operator even with different IP addresses. Therefore, we should strive to find more authentic and reliable IPs.
3. Recorded Operational Behaviors
This is a detection method that many overlook but actually carries significant weight in platform risk control.
If abnormal operations are detected due to the aforementioned information leaks, platforms will most likely identify patterns such as: mouse movement trajectory and rhythm, page dwell time distribution, habitual click positions, typing speed and rhythm, and regular login time periods.
Moreover, if multiple accounts log in at similar times, follow nearly identical operation paths, or have similar browsing habits, the system is more likely to determine that they are controlled by the same person.
III. Why Is Fingerprint Spoofing Becoming Increasingly Strict?
Platform risk control systems are evolving and no longer rely solely on static fingerprints. In the early days, platforms mainly identified information such as browser version, operating system, and IP address.
Now, however, they rely more on fingerprint stability and naturalness (whether it mimics a real user's device), similarity clustering between fingerprints, long-term behavioral trajectory analysis, and device reputation scores.
Even if a device has a unique fingerprint, it will still be marked as a high-risk environment if its overall performance does not resemble a real and natural device. This means we need to conduct in-depth spoofing of information across more dimensions.
IV. How to Prevent Account Association?
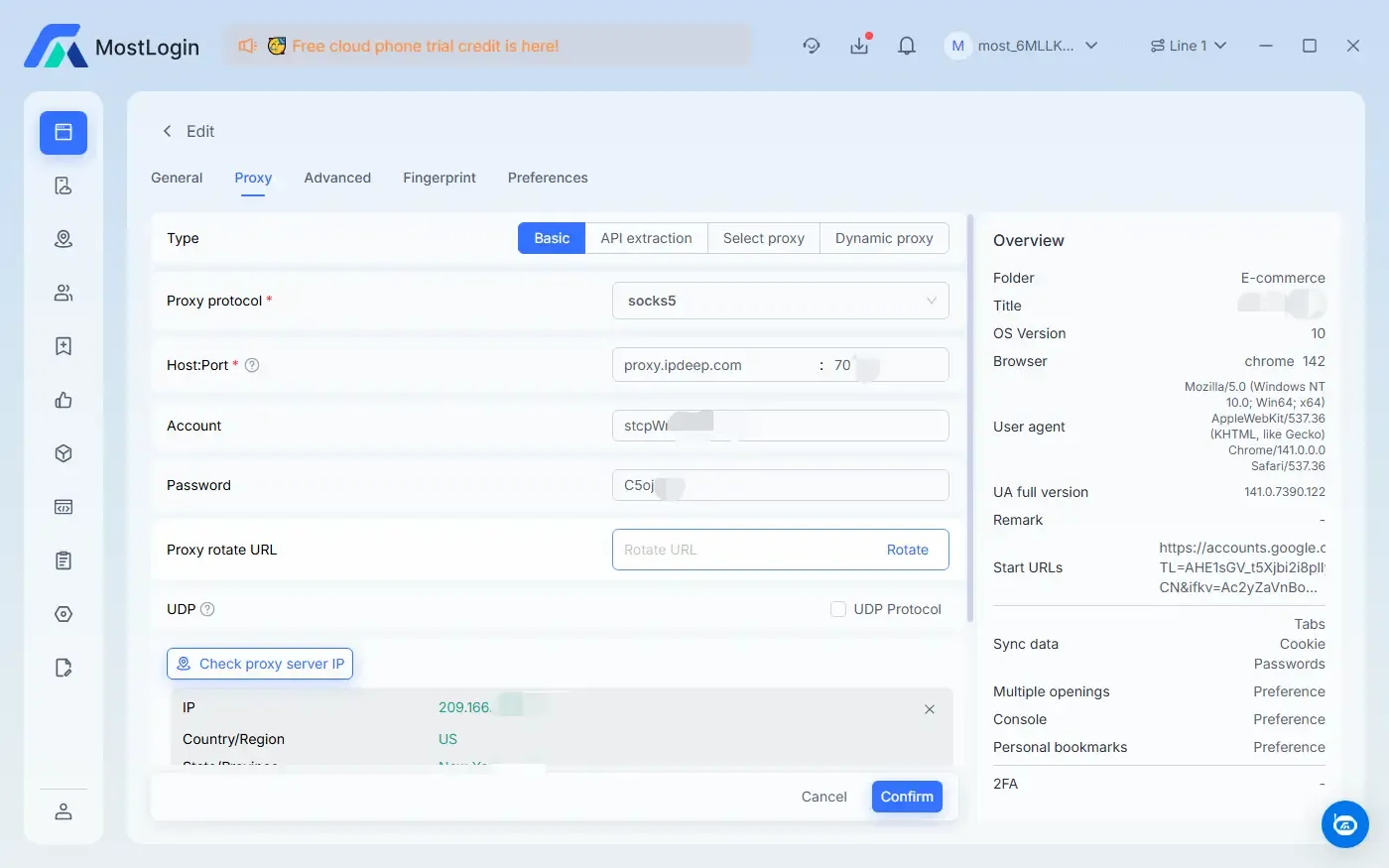
We recommend upgrading both the IP configuration and the anti-association browser. For example, use the more powerful MostLogin Anti-Detection Browser, which not only modifies User-Agent, Canvas fingerprint, WebGL parameters, time zones, languages and other basic information, but also achieves more robust spoofing effects.
As can be seen here, the browser displays detailed information about various browser fingerprints. It also supports deep IP binding and configures relevant parameters based on the bound IP. This not only makes our device information appear more authentic, but also makes it far more difficult for platform risk control mechanisms to detect our multi-account operations.
Currently, MostLogin Anti-Detection Browser also offers the "Forerunner Program", which provides free access to all features except cloud phone services. It is extremely suitable for individuals and teams to experience.
Summary
In summary, an anti-association environment is not a one-time configuration for permanent security. When identifying account association, platforms make comprehensive judgments based on multiple dimensions including device characteristics, network quality, behavioral patterns, and long-term stability. To truly reduce the probability of association, it is essential to make each account's environment, network, and behaviors as close to those of an independent, real user as possible.
FAQs
Why are accounts still associated even with an anti-association browser?
Because platforms comprehensively identify device, network, and behavioral data, not just browser fingerprints.
Is it safe as long as browser fingerprints are different?
No, fingerprints are only one factor; the naturalness of the overall environment is more important.
Why can accounts still be judged as associated with different IPs?
Platforms analyze the network characteristics and source type of IPs, not just the IP addresses themselves.
Do platforms really record operational behaviors?
Yes, mouse trajectories, operation rhythms, and login regularities are all important identification signals.
Why is fingerprint spoofing becoming increasingly ineffective now?
Because platforms have upgraded from static fingerprint identification to long-term behavioral and stability analysis.
What is the core idea to reduce the risk of account association?
Make the environment, network, and behaviors of each account more like those of an independent, real user.
MostLogin Anti-Detection Browser helps users solve common pain points such as multi-account management, environment isolation, and account risk control.
For operational questions, please refer to the Official Help Documentation


