Many senior marketers think that when managing multiple accounts, using a different IP for each account will prevent the platform from detecting that they are operated by the same person. However, with the current risk control mechanisms, such ideas or practices can no longer avoid detection and association.
Today, we will explain clearly from the perspective of technology and risk control logic why accounts are still associated even with different IPs, as well as other relevant content.
1. IP is only one signal for account association
IP addresses are indeed important, but in modern risk control systems, they are just one indicator among many identification dimensions. We can think of a platform's risk control system as a comprehensive scoring system that evaluates multiple factors simultaneously: device environment, browser characteristics, network features, behavior patterns, interaction relationships between accounts, and more.
IP only accounts for a small part of the weight and is not a decisive factor. Therefore, when we change the IP but keep other environments highly similar, the system will see this more as the same person switching networks rather than completely different users.
2. Why does it still look like the same person with different IPs?
1. Unchanged device fingerprint
Even with different IPs, if you use the same computer or browser environment, the platform can still identify a large number of similar features, such as:
Browser fingerprint (Canvas, WebGL, font rendering, etc.)
Screen resolution and zoom ratio
Operating system version
Graphics driver-related features
Audio processing features
These combine to form a relatively stable device profile. When multiple accounts come from different IPs but have almost identical device profiles, the platform is more likely to judge that they are operated by the same device.
2. Network type is more important than the IP itself
Many people only focus on whether the IP address is different, but ignore deeper network features, such as whether they come from the same operator network (ASN), whether they all belong to data center or proxy networks, network latency and stability patterns, DNS resolution paths, local network information exposed by WebRTC, and so on.
For a simple example, two accounts have different IPs but both come from proxy networks of the same region and type, coupled with similar network quality features. In the eyes of the risk control system, this does not look like two ordinary home users, but more like the same operator using a similar network resource pool.
3. Identical browser and system environment
Even if you change the IP, if the browser environment of each account shows highly consistent features, such as the same browser version, the same plug-in combination, the same language and time zone settings, and a similar list of system fonts. These details add up to form a significant environmental similarity.
The risk control system does not require this information to be 100% the same; as long as the similarity is consistently higher than that of normal random users, it may be classified as an associated device group.
4. Behavior patterns reveal the same operator
This is a point that many people are completely unaware of but has an actually very high weight - behavior fingerprint. Through long-term data analysis, the platform can find that multiple accounts always log in at similar time periods, have highly similar browsing paths, close operation rhythms (dwell time, click order), and similar typing rhythms or interaction frequencies.
These cannot be judged by a single login, but are based on a long-term behavior statistical model. Even with different IPs, as long as the behavior is like that of the same person, the system may still make an association judgment.
5. Business-level overlap between accounts
In addition to the technical level, the platform also analyzes whether there are business relationships between accounts, such as using the same shipping address or contact information, binding similar payment methods, publishing highly similar content, following each other, and operating on each other's accounts.
These data form a relationship graph within the platform; once multiple accounts have a high degree of overlap at the business level, they can be easily identified as associated even with different IPs.
3. Why did changing IP solve the problem before?
Because the platform's risk control system has upgraded from single-point identification to multi-dimensional identification. In the early days, platforms may have mainly relied on IP, browser version, and whether they have logged in to the same device. Now, more attention is paid to the long-term stability of the device, whether the environment is natural and real, whether the behavior conforms to the characteristics of independent users, and whether there are group behavior patterns among multiple accounts.
With the upgrade of the identification logic, the effect of simply changing the IP has gradually become more and more limited, and thus it is no longer possible to completely prevent detection.
4. How can we avoid account association?
Using an anti-detection browser is currently the best solution. For example, the MostLogin Anti-detection Browser can not only help us protect the security between accounts, but also create multiple different window environments to use with IPs, making it convenient for us to log in and manage multiple accounts.
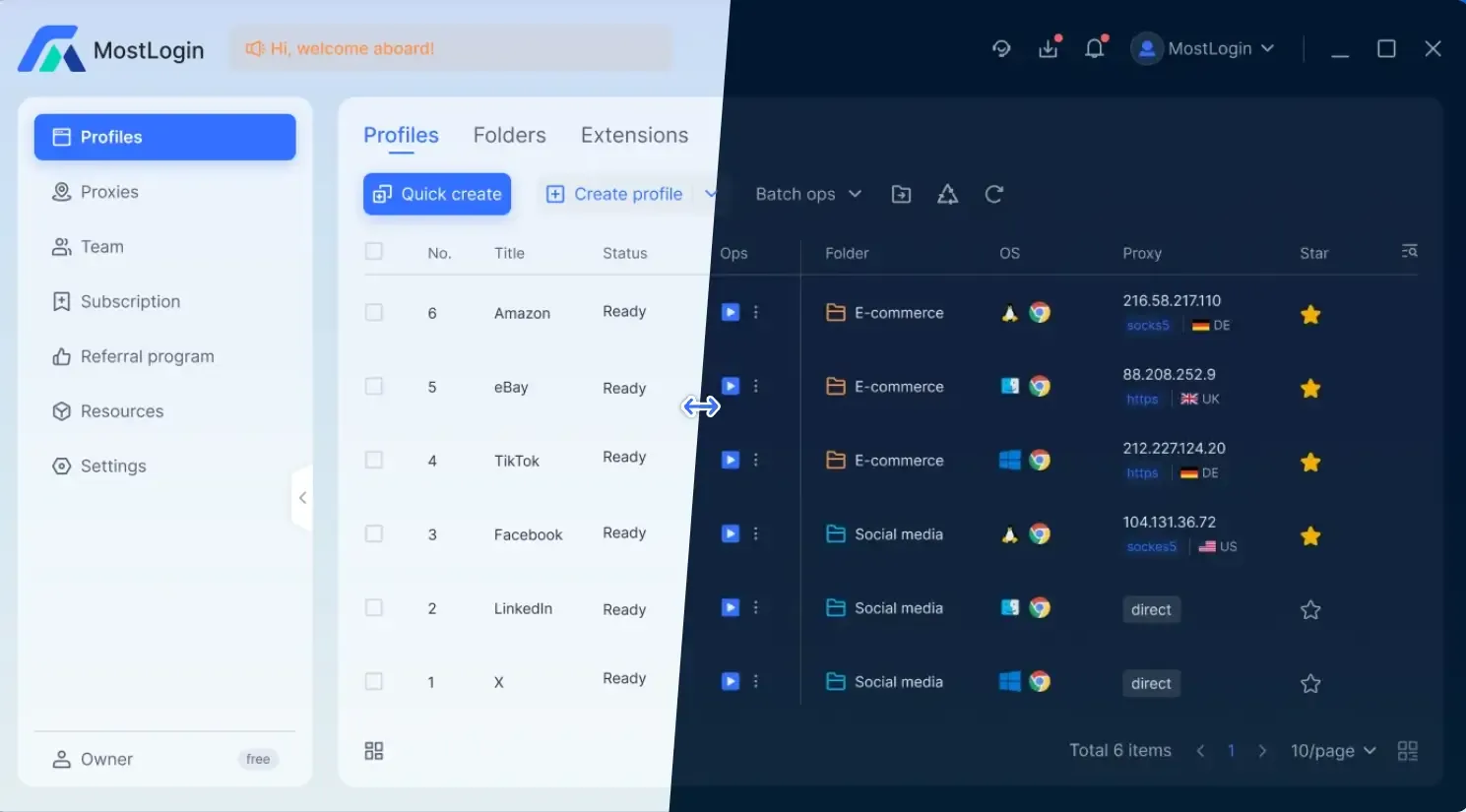
Moreover, with the MostLogin Anti-detection Browser, we can also use it with proxy IPs we have used before, helping us protect our accounts in a more comprehensive way. Reasonably matching the browser environment and IP proxy information is very important for the overall security of the account.
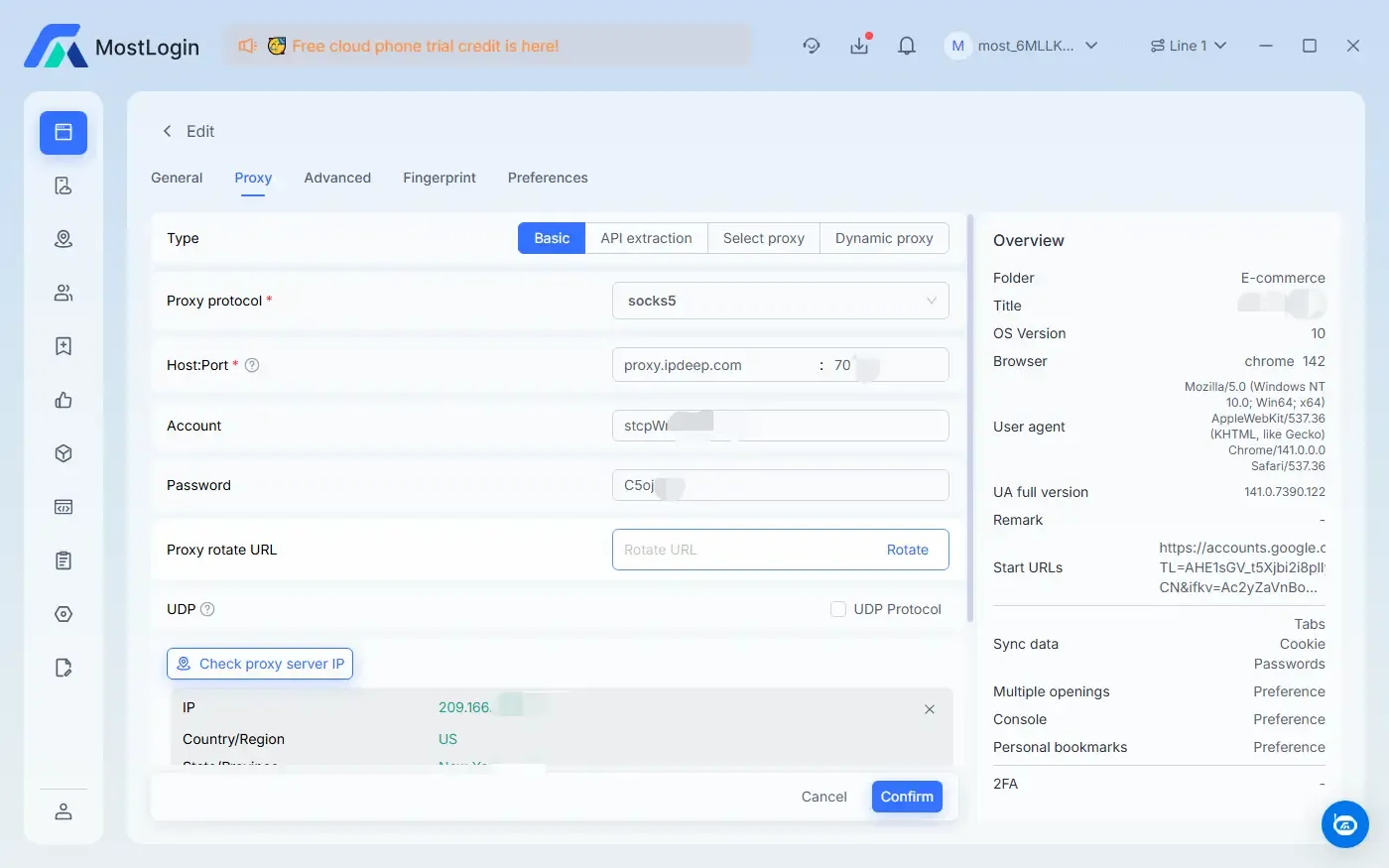
At present, the MostLogin Fingerprint Browser has a "Forerunner Program". Except for the cloud phone service, all fingerprint browser functions are free. Personal users and teams are welcome to experience and use it!
Summary
Overall, changing to different IPs cannot fundamentally solve the problem of account association, because in the current platform risk control system, IP is only one of many identification signals. Device fingerprints, browser environment, network type, behavior patterns, and business relationships between accounts all jointly participate in the association judgment. Only by using the MostLogin Fingerprint Browser to achieve systematic isolation from the perspective of the overall environment and usage habits can we truly reduce the risk of account association.
FAQs
Is it definitely safe to use different IPs for different accounts?
Not necessarily. IP is only one of the identification factors and cannot alone determine whether accounts are associated.
Why does it still look like the same person with different IPs?
Because the device fingerprint and browser environment are highly consistent.
Is network type more important than IP address?
Yes, platforms focus on analyzing the type and stability characteristics of network sources.
Can behavior patterns really lead to account association?
Yes, long-term similar operating behaviors are a high-weight association signal.
Can accounts be associated even without interaction between them?
Yes, there is a risk as long as the environment and behavior are highly similar.
What is the core idea to avoid account association?
Make each account look more like an independent and real user in terms of device, network and behavior.
The MostLogin Anti-detection Browser tool helps users solve high-frequency problems such as multi-account operation, environment isolation, and account risk control.
For operation questions, please refer to the Official Help Documentation


